_Follow along with this video:_ --- ### Weak Randomness Overview This will be a quick overview, but there are a view ways that Weak Randomness can cause issues. Let's actually take a moment to go back to `Slither` because, if you can believe it, `Slither` will actually catch this for us. ```bash slither . ``` Running slither as above we can see it's output contains the following: 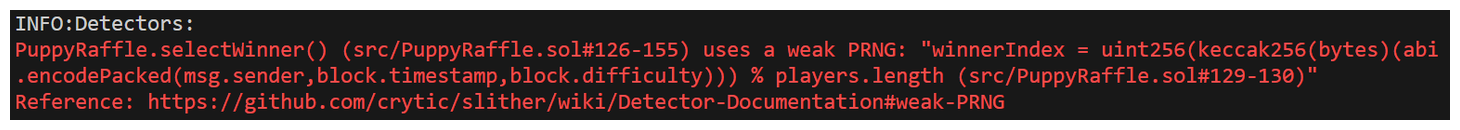 So what is this detector telling us - that `PuppyRaffle.sol` is using weak PRNG or Pseudo Random Number Generation. We can navigate to the [**link provided**](https://github.com/crytic/slither/wiki/Detector-Documentation#weak-PRNG) for more information and a simplified example of this vulnerability. 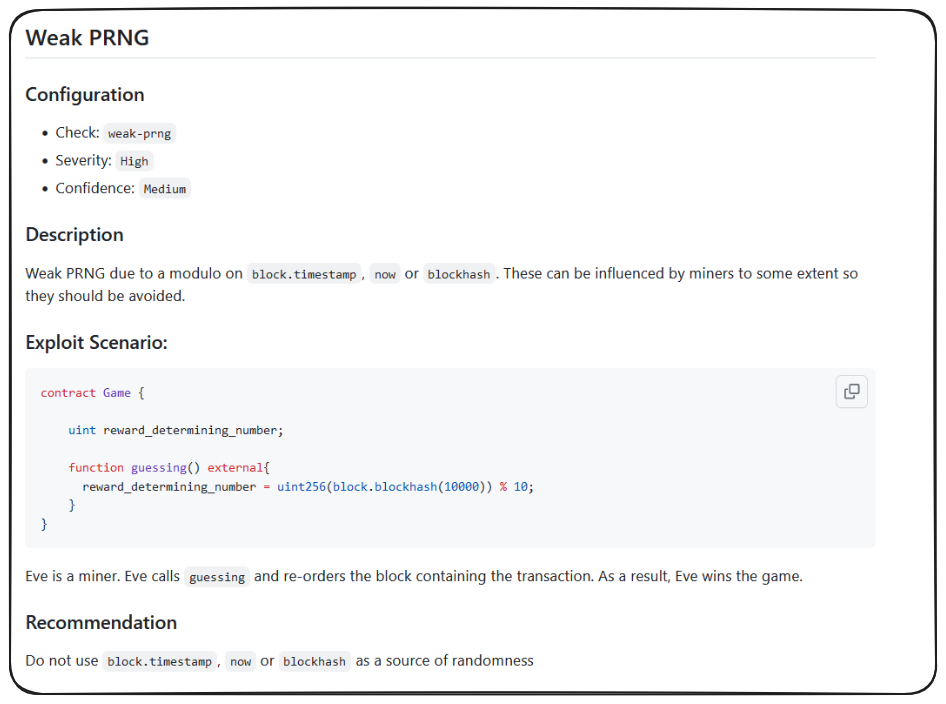 Beyond what's outlined here as a concern - that miners can influence global variables favorable - there's a lot more _weirdness_ that goes into random numbers on-chain. If you've seen any of my other content, you know that Chainlink VRF is a solution for this problem, and I encourage you to check out the [**documentation**](https://docs.chain.link/vrf) for some additional learnings. ### Remix Examples Return to our [**sc-exploits-minimized**](https://github.com/Cyfrin/sc-exploits-minimized) repo and we've included a link to a [**Remix example**](https://remix.ethereum.org/#url=https://github.com/Cyfrin/sc-exploits-minimized/blob/main/src/weak-randomness/WeakRandomness.sol&lang=en&optimize=false&runs=200&evmVersion=null&version=soljson-v0.8.20+commit.a1b79de6.js) of this vulnerability. > This contract is available for local testing as well [**here**](https://github.com/Cyfrin/sc-exploits-minimized/blob/main/src/weak-randomness/WeakRandomness.sol). Looking at the `Remix` example, we can see it's doing something very similar to what `PuppyRaffle` is doing ```js uint256 randomNumber = uint256(keccak256(abi.encodePacked(msg.sender, block.prevrandao, block.timestamp))); ``` In this declaration we're taking 3 variables: - msg.sender - block.prevrandao - block.timestamp We're hashing these variables and casting the result as a uint256. The problem exists in that the 3 variables we're deriving our number from are able to be influenced or anticipated such that we can predict what the random number will be. The test set up in [**sc-exploits-minimized**](https://github.com/Cyfrin/sc-exploits-minimized) may look a little silly, but what's trying to be conveyed is that generating the same random number in a single block is another example of how this vulnerability can be exploited. ```js // For this test, a user could just deploy a contract that guesses the random number... // by calling the random number in the same block!! function test_guessRandomNumber() public { uint256 randomNumber = weakRandomness.getRandomNumber(); assertEq(randomNumber, weakRandomness.getRandomNumber()); } ``` ### Wrap Up In short - the blockchain is deterministic. Using on-chain variables and pseudo random number generation leaves a protocol open to exploits whereby an attacker can predict or manipulate the 'random' value. There multiple ways that weak randomness can be exploited, and we'll be going through them in the next lesson!
Follow along with this video:
Weak Randomness Overview
This will be a quick overview, but there are a view ways that Weak Randomness can cause issues.
Let's actually take a moment to go back to Slither because, if you can believe it, Slither will actually catch this for us.
Running slither as above we can see it's output contains the following:

So what is this detector telling us - that PuppyRaffle.sol is using weak PRNG or Pseudo Random Number Generation. We can navigate to the link provided for more information and a simplified example of this vulnerability.

Beyond what's outlined here as a concern - that miners can influence global variables favorable - there's a lot more weirdness that goes into random numbers on-chain.
If you've seen any of my other content, you know that Chainlink VRF is a solution for this problem, and I encourage you to check out the documentation for some additional learnings.
Remix Examples
Return to our sc-exploits-minimized repo and we've included a link to a Remix example of this vulnerability.
This contract is available for local testing as well here.
Looking at the Remix example, we can see it's doing something very similar to what PuppyRaffle is doing
In this declaration we're taking 3 variables:
msg.sender
block.prevrandao
block.timestamp
We're hashing these variables and casting the result as a uint256. The problem exists in that the 3 variables we're deriving our number from are able to be influenced or anticipated such that we can predict what the random number will be.
The test set up in sc-exploits-minimized may look a little silly, but what's trying to be conveyed is that generating the same random number in a single block is another example of how this vulnerability can be exploited.
Wrap Up
In short - the blockchain is deterministic. Using on-chain variables and pseudo random number generation leaves a protocol open to exploits whereby an attacker can predict or manipulate the 'random' value.
There multiple ways that weak randomness can be exploited, and we'll be going through them in the next lesson!
Exploit: Weak Randomness
Dive into PuppyRaffle's weak randomness. Patrick emphasizes use of secure sources like Chainlink VRF.
Previous lesson
Previous
Next lesson
Next
Duration: 25min
Duration: 1h 19min
Duration: 35min
Duration: 2h 28min
Duration: 5h 04min
Duration: 5h 23min
Duration: 4h 33min
Duration: 2h 01min
Duration: 1h 41min