_Follow along with this video:_ --- ### Exploits, but smaller ```js // Check for duplicates for (uint256 i = 0; i < players.length - 1; i++) { for (uint256 j = i + 1; j < players.length; j++) { require(players[i] != players[j], "PuppyRaffle: Duplicate player"); } } ``` This code above is going to cause something called a Denial of Service or DOS. In order to get a better understanding of this bug, let's look at a _minimized_ example of it. If you reference the [**sc-exploits-minimized**](https://github.com/Cyfrin/sc-exploits-minimized) repo, half way down you should see something like what's pictured below. 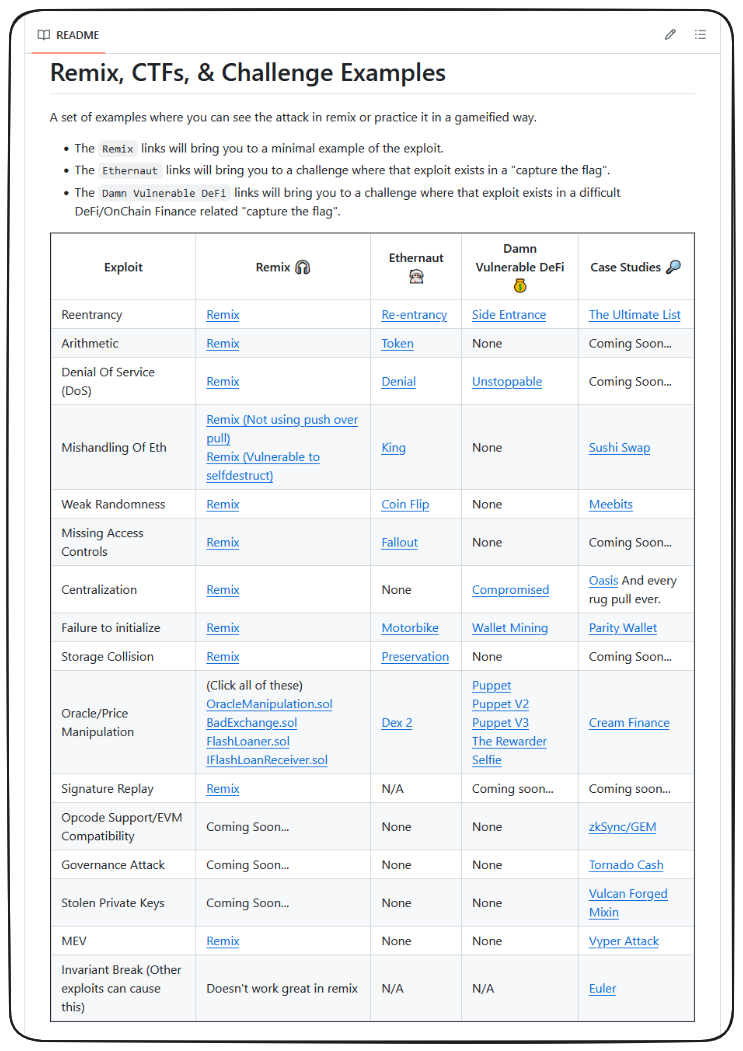 This is an amazing resource to test your skills in general and familiarize yourself with common exploits. Additionally, the `src` folder of `sc-exploits-minimized` contains minimalistic examples of a variety of vulnerabilities as well. For now, let's check out the [**Remix example**](https://remix.ethereum.org/#url=https://github.com/Cyfrin/sc-exploits-minimized/blob/main/src/denial-of-service/DoS.sol&lang=en&optimize=false&runs=200&evmVersion=null&version=soljson-v0.8.20+commit.a1b79de6.js) of the Denial of Service exploit in the next lesson.
Follow along with this video:
Exploits, but smaller
This code above is going to cause something called a Denial of Service or DOS.
In order to get a better understanding of this bug, let's look at a minimized example of it. If you reference the sc-exploits-minimized repo, half way down you should see something like what's pictured below.

This is an amazing resource to test your skills in general and familiarize yourself with common exploits. Additionally, the src folder of sc-exploits-minimized contains minimalistic examples of a variety of vulnerabilities as well.
For now, let's check out the Remix example of the Denial of Service exploit in the next lesson.
sc-exploits-minimized
Introducing the sc-exploits-minimized repo, a compilation of common smart contract vulnerability examples.
Previous lesson
Previous
Next lesson
Next
Duration: 25min
Duration: 1h 19min
Duration: 35min
Duration: 2h 28min
Duration: 5h 04min
Duration: 5h 23min
Duration: 4h 33min
Duration: 2h 01min
Duration: 1h 41min