5/5
_Follow along with this video:_ --- ### Parametric Rules In this lesson we'll go through a `parametric` formal verification example. You can read more about Parametric rules [**here in the Certora docs**](https://docs.certora.com/en/latest/docs/user-guide/parametric.html), but in brief they're rules which take ambiguous methods as parameters and differ from invariants in two key ways: 1. Invariants are also testing after the constructor 2. Invariants are used to assert properties of the storage (between function calls), while parametric rules are used to assert properties of _changes_ in the storage (caused by function calls). Ultimately, any rule which contains an arbitrary method can be considered a `parametric rule`. What this allows us to do is configure a rule which calls any random method in our scene, we can further abstract this and pass the method random calldata and environment variables. A minimalistic example of this would look something like: ```js rule sanity { method f; env e; calldataarg arg; f(e, arg); satisfy true; } ``` So, let's set up a simple example that applies to our NftMock. This example will be a little silly, as we expect it to fail, but it should demonstrate the concept clearly enough. ```js rule no_change_to_total_supply(method f) { uint256 totalSupplyBefore = totalSupply(); env e; calldataarg arg; f(e, arg); assert totalSupply() == totalSupplyBefore, "Total supply should not change!" } ``` > ❗ **NOTE** > Passing a variable as an input parameter is almost identical to defining it within the rule body. What's cool about this set up is that it nearly functions like our `stateful fuzz testing`. `Certora` is going to `HAVOC` the storage variables (replace them with random values), and simulate the contract in different states. At each step it calls a method, our rule is going to assure that the `totalSupply` variable never changes. Again, we expect this to fail, since the contract contains a mint function, but we can run this to see how it performs. ```bash certoraRun ./certora/conf/NftMock.conf ``` 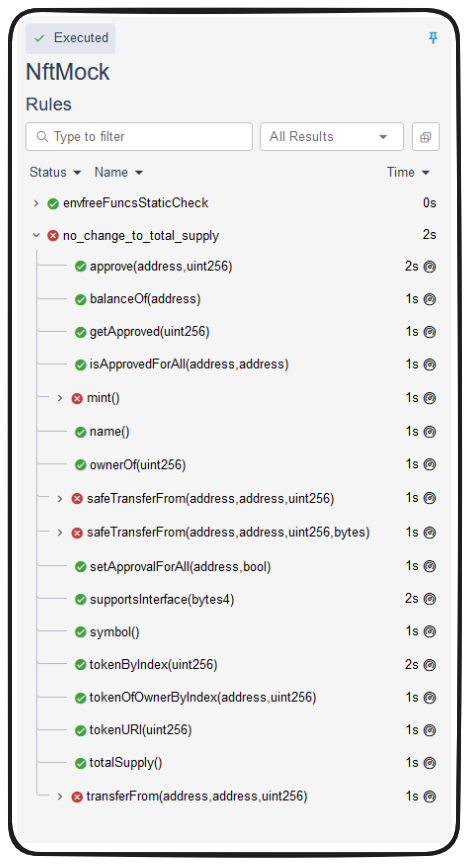 As expected, we can see this fails, but by taking a closer look we can ascertain why and better understand the conclusion the prover came to. Intuitively we know that the `totalSupply` of `NftMock` is going to increase with `mint` function calls, but perhaps less intuitively the prover has pointed out that callback functions through `onERC721Received` can recursively call the `mint` function _also_ calling this assertion to fail! ### Wrap Up Clearly `parametric rules` can be a powerful tool in an auditor's belt when performing formal verification with `Certora`. We've covered a few concepts in our little trial run through `NftMock` verification, so let's recap in the next lesson. See you there!
Follow along with this video:
Parametric Rules
In this lesson we'll go through a parametric formal verification example. You can read more about Parametric rules here in the Certora docs, but in brief they're rules which take ambiguous methods as parameters and differ from invariants in two key ways:
Invariants are also testing after the constructor
Invariants are used to assert properties of the storage (between function calls), while parametric rules are used to assert properties of changes in the storage (caused by function calls).
Ultimately, any rule which contains an arbitrary method can be considered a parametric rule. What this allows us to do is configure a rule which calls any random method in our scene, we can further abstract this and pass the method random calldata and environment variables. A minimalistic example of this would look something like:
So, let's set up a simple example that applies to our NftMock. This example will be a little silly, as we expect it to fail, but it should demonstrate the concept clearly enough.
❗ NOTE
Passing a variable as an input parameter is almost identical to defining it within the rule body.
What's cool about this set up is that it nearly functions like our stateful fuzz testing. Certora is going to HAVOC the storage variables (replace them with random values), and simulate the contract in different states. At each step it calls a method, our rule is going to assure that the totalSupply variable never changes.
Again, we expect this to fail, since the contract contains a mint function, but we can run this to see how it performs.

As expected, we can see this fails, but by taking a closer look we can ascertain why and better understand the conclusion the prover came to. Intuitively we know that the totalSupply of NftMock is going to increase with mint function calls, but perhaps less intuitively the prover has pointed out that callback functions through onERC721Received can recursively call the mint function also calling this assertion to fail!
Wrap Up
Clearly parametric rules can be a powerful tool in an auditor's belt when performing formal verification with Certora. We've covered a few concepts in our little trial run through NftMock verification, so let's recap in the next lesson.
See you there!
Parametric Rules
In this lesson, Patrick explains Parametric rules and how they're used with respect to Certora's prover.
Previous lesson
Previous
Next lesson
Next
Course Overview
About the course
What you'll learn
Assembly
Writing smart contracts using Huff and Yul
Ethereum Virtual Machine OPCodes
Formal verification testing
Smart contract invariant testing
Halmos, Certora, Kontrol
Course Description
Who is this course for?
- Smart contract security researchers
- Advanced Smart contract engineers
- Chief Security Officiers
- Security professionals
Potential Careers
Security researcher
$49,999 - $120,000 (avg. salary)
Smart Contract Auditor
$100,000 - $200,000 (avg. salary)
Meet your instructors
Guest lecturers:
Last updated on February 1, 2026
Duration: 30min
Duration: 4h 40min
Duration: 3h 58min
Duration: 1h 56min
Course Overview
About the course
What you'll learn
Assembly
Writing smart contracts using Huff and Yul
Ethereum Virtual Machine OPCodes
Formal verification testing
Smart contract invariant testing
Halmos, Certora, Kontrol
Course Description
Who is this course for?
- Smart contract security researchers
- Advanced Smart contract engineers
- Chief Security Officiers
- Security professionals
Potential Careers
Security researcher
$49,999 - $120,000 (avg. salary)
Smart Contract Auditor
$100,000 - $200,000 (avg. salary)
Meet your instructors
Guest lecturers:
Last updated on February 1, 2026
