_Follow along with this video:_ --- ### MEV - Boss Bridge Now you're starting to see the picture, and the Boss Bridge MEV becomes clear. 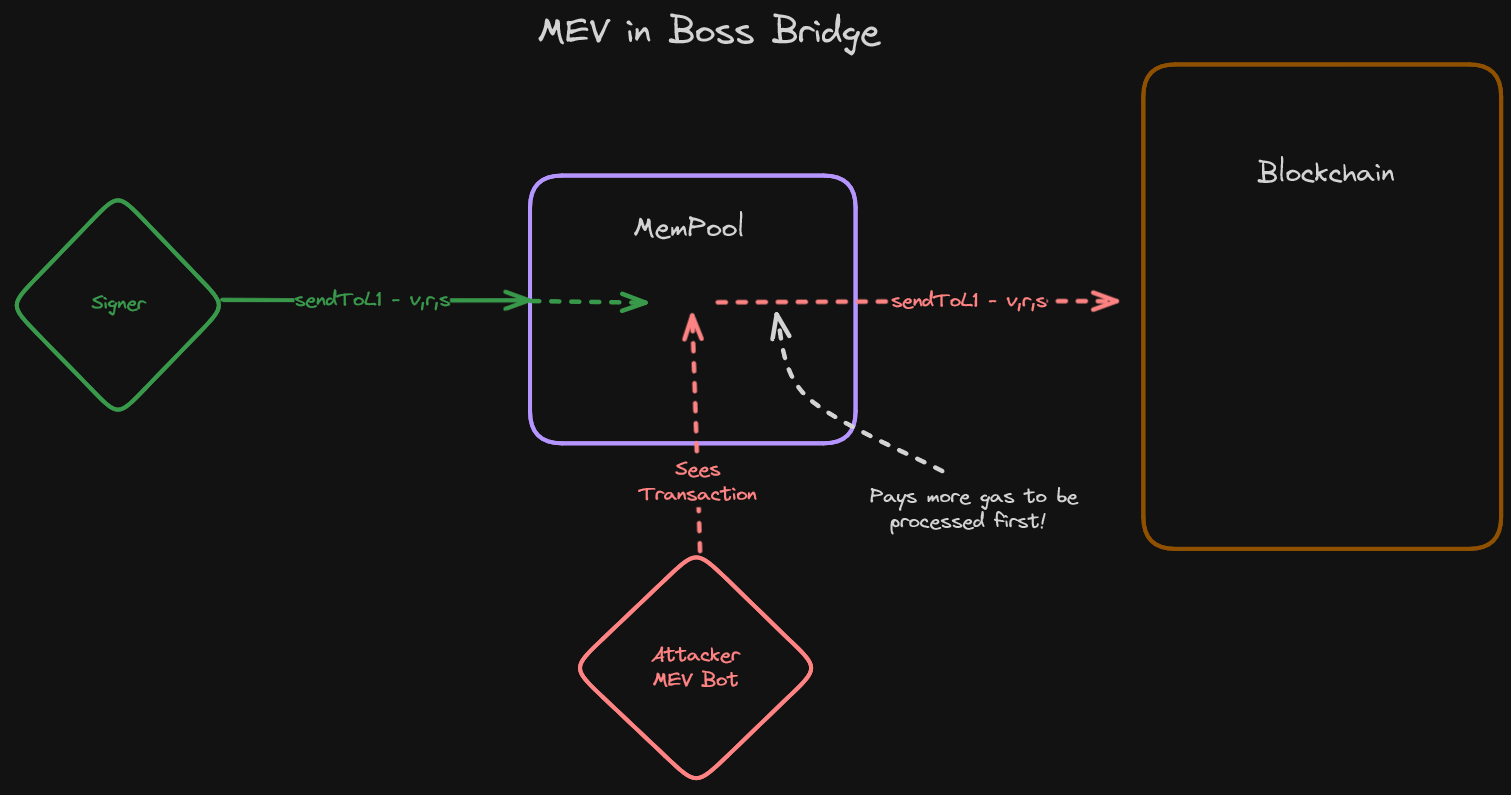 Similarly to the Signature Replay attack, a malicious actor could see a signer's call to sendToL1 pending in the MemPool. With access to the signature sent in the transaction, it can be front run, causing the sendToL1 transaction to happen unexpectedly, or multiple times. Without specifying some sort of protection against this (leveraging a nonce, requiring the signer to call it first etc), Boss Bridge is wide open to these kinds of vulnerabilities. ### Wrap Up Every single once of the protocols we reviewed was at risk of being exploited through MEV vulnerabilities!? Hopefully it's clear how pervasive these security risks can be. In the next lesson I'll demonstrate a live example of being rekt by an MEV Bot. You won't want to miss it! See you there!
Follow along with this video:
MEV - Boss Bridge
Now you're starting to see the picture, and the Boss Bridge MEV becomes clear.

Similarly to the Signature Replay attack, a malicious actor could see a signer's call to sendToL1 pending in the MemPool. With access to the signature sent in the transaction, it can be front run, causing the sendToL1 transaction to happen unexpectedly, or multiple times.
Without specifying some sort of protection against this (leveraging a nonce, requiring the signer to call it first etc), Boss Bridge is wide open to these kinds of vulnerabilities.
Wrap Up
Every single once of the protocols we reviewed was at risk of being exploited through MEV vulnerabilities!?
Hopefully it's clear how pervasive these security risks can be.
In the next lesson I'll demonstrate a live example of being rekt by an MEV Bot. You won't want to miss it! See you there!
MEV: BossBridge
MEV Vulnerabilities in Boss Bridge discussed!
Previous lesson
Previous
Next lesson
Next
Duration: 25min
Duration: 1h 19min
Duration: 35min
Duration: 2h 28min
Duration: 5h 04min
Duration: 5h 23min
Duration: 4h 33min
Duration: 2h 01min
Duration: 1h 41min