_Follow along with this video:_ --- ### MEV - Thunder Loan Surely Thunder Loan is safe from MEV attacks! Everything happens so fast, there's no way someone could step in to affect anything, right? Afraid not. `Thunder Loan` is susceptible to something called a `sandwich attack`. By closely monitoring the `mempool`, a malicious actor would be able to see a pending flash loan and exploit `Thunder Loan`'s reliance on the TSwap protocol as an oracle by swapping the loaned tokens, `front running` the flash loan, and subsequently altering the expected fees associated with it. The malicious actor can then **swap back** (this is called `back running`) before the loan's repayment checks TSwap again! This would drastically impact the flash loan experience in Thunder Loan and may cause several of them to fail, or worse - cost victims a tonne in unexpected fees. 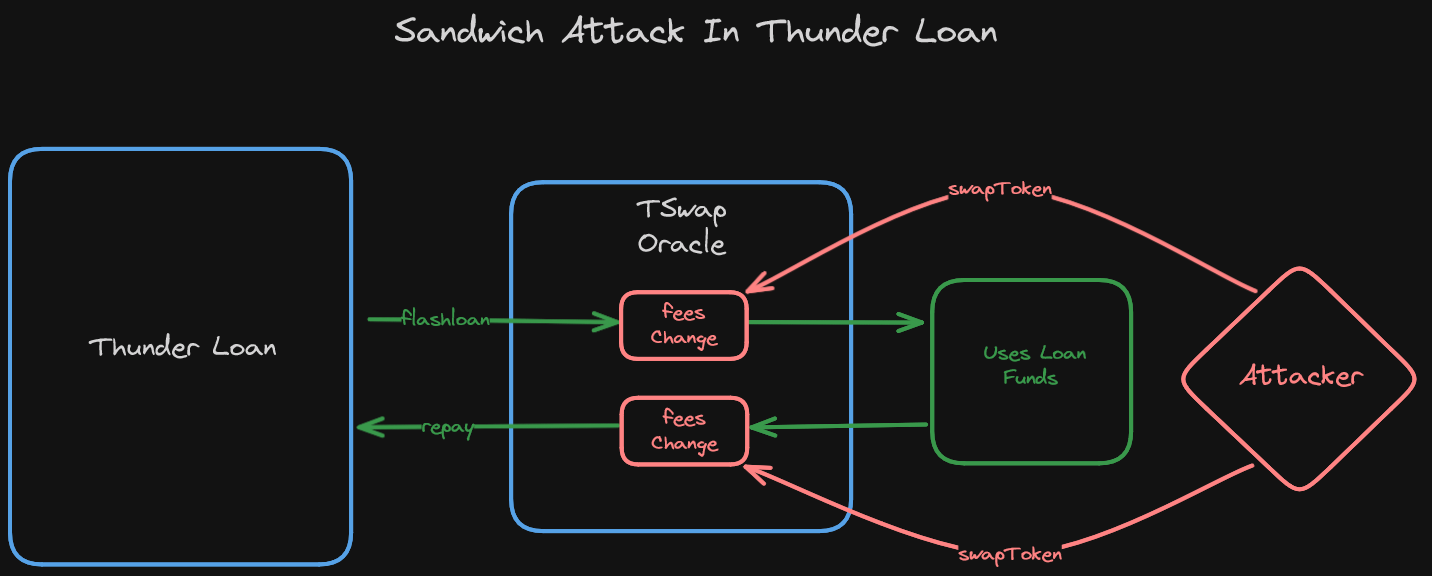 ### Wrap Up Things aren't looking good... we better check `Boss Bridge`! See you there, in the next lesson!
Follow along with this video:
MEV - Thunder Loan
Surely Thunder Loan is safe from MEV attacks! Everything happens so fast, there's no way someone could step in to affect anything, right?
Afraid not.
Thunder Loan is susceptible to something called a sandwich attack.
By closely monitoring the mempool, a malicious actor would be able to see a pending flash loan and exploit Thunder Loan's reliance on the TSwap protocol as an oracle by swapping the loaned tokens, front running the flash loan, and subsequently altering the expected fees associated with it.
The malicious actor can then swap back (this is called back running) before the loan's repayment checks TSwap again! This would drastically impact the flash loan experience in Thunder Loan and may cause several of them to fail, or worse - cost victims a tonne in unexpected fees.

Wrap Up
Things aren't looking good... we better check Boss Bridge! See you there, in the next lesson!
MEV: ThunderLoan
MEV Vulnerabilities in Thunder Loan discussed!
Previous lesson
Previous
Next lesson
Next
Duration: 25min
Duration: 1h 19min
Duration: 35min
Duration: 2h 28min
Duration: 5h 04min
Duration: 5h 23min
Duration: 4h 33min
Duration: 2h 01min
Duration: 1h 41min