5/5
_Follow along with this video:_ --- ### Accessing our Call Data's Function Selector We're already starting to code using pure opcodes, very exciting! Alright, eventually someone is going to send our contract some `calldata` and we need to determine what to do with it. We do this by deriving the `function selector` from the first 4 bytes of the `calldata` being sent. Fortunately we have an opcode just for this purpose! `calldataload` will allow us to load our `calldata` onto the stack. 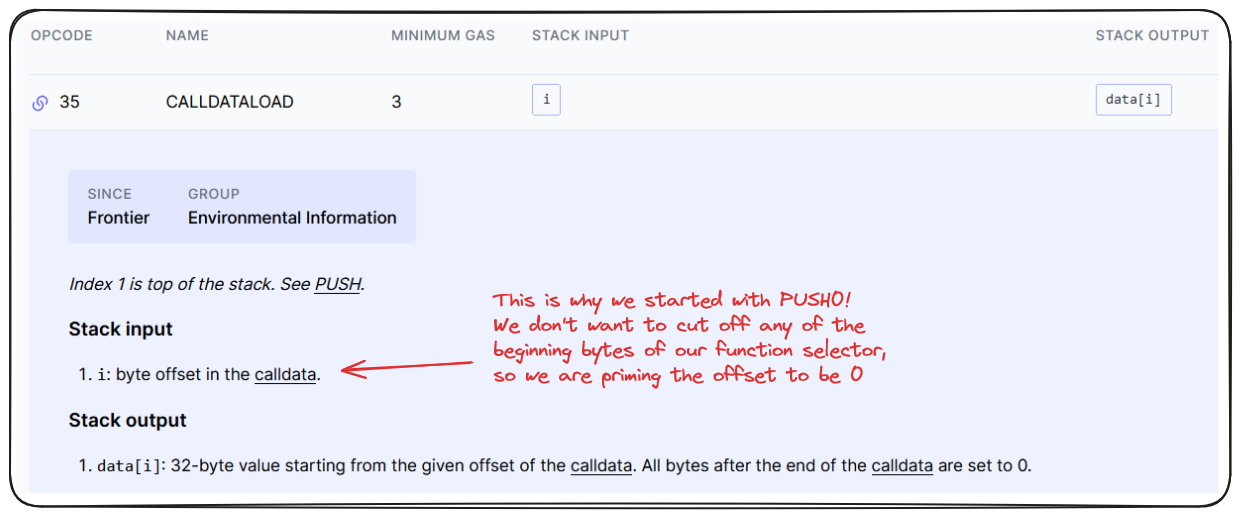 So we can see the `calldataload` opcode is going to take whatever is on top of our stack, and use it as the `bytes offset`. Since we want to capture our _whole_ function selector, we set this offset to 0 by using `PUSH0` as the operation prior to `calldataload`. ### Keeping Track of the Stack Something that I like to do is leverage comments in my code as a visual means to keep track of what's on my stack. Here's an example. ```js #define macro MAIN() = takes(0) returns(0) { 0x00 // [0] 0x02 // TOP [2,0] BOTTOM } ``` In this example, I keep track of my stack and what's in it through commenting an array next to these operations. By adding and removing items in this visual way, you won't need to remember the order your stack is in as you code. Our Huff contract utilizing the `calldataload` opcode should look like this: ```js #define macro MAIN() = takes(0) returns(0) { 0x00 // [0] calldataload // [calldata] } ``` We can see that the `calldataload` opcode removed the `PUSH0` and replaced the first item in our stack with the first 32 bytes of `calldata` our contract was sent!
Follow along with this video:
Accessing our Call Data's Function Selector
We're already starting to code using pure opcodes, very exciting!
Alright, eventually someone is going to send our contract some calldata and we need to determine what to do with it. We do this by deriving the function selector from the first 4 bytes of the calldata being sent.
Fortunately we have an opcode just for this purpose! calldataload will allow us to load our calldata onto the stack.

So we can see the calldataload opcode is going to take whatever is on top of our stack, and use it as the bytes offset. Since we want to capture our whole function selector, we set this offset to 0 by using PUSH0 as the operation prior to calldataload.
Keeping Track of the Stack
Something that I like to do is leverage comments in my code as a visual means to keep track of what's on my stack. Here's an example.
In this example, I keep track of my stack and what's in it through commenting an array next to these operations. By adding and removing items in this visual way, you won't need to remember the order your stack is in as you code.
Our Huff contract utilizing the calldataload opcode should look like this:
We can see that the calldataload opcode removed the PUSH0 and replaced the first item in our stack with the first 32 bytes of calldata our contract was sent!
Calldataload
A detailed guide to the Call Data Load OpCode - The lesson covers the basic concepts behind Call Data Load and how to implement it in Huff, a Solidity alternative, using the EVM.codes website as a reference. It also discusses how to visualize the stack in Huff code using comments to help with debugging.
Previous lesson
Previous
Next lesson
Next
Course Overview
About the course
What you'll learn
Assembly
Writing smart contracts using Huff and Yul
Ethereum Virtual Machine OPCodes
Formal verification testing
Smart contract invariant testing
Halmos, Certora, Kontrol
Course Description
Who is this course for?
- Smart contract security researchers
- Advanced Smart contract engineers
- Chief Security Officiers
- Security professionals
Potential Careers
Security researcher
$49,999 - $120,000 (avg. salary)
Smart Contract Auditor
$100,000 - $200,000 (avg. salary)
Meet your instructors
Guest lecturers:
Last updated on February 1, 2026
Duration: 30min
Duration: 4h 40min
Duration: 3h 58min
Duration: 1h 56min
Course Overview
About the course
What you'll learn
Assembly
Writing smart contracts using Huff and Yul
Ethereum Virtual Machine OPCodes
Formal verification testing
Smart contract invariant testing
Halmos, Certora, Kontrol
Course Description
Who is this course for?
- Smart contract security researchers
- Advanced Smart contract engineers
- Chief Security Officiers
- Security professionals
Potential Careers
Security researcher
$49,999 - $120,000 (avg. salary)
Smart Contract Auditor
$100,000 - $200,000 (avg. salary)
Meet your instructors
Guest lecturers:
Last updated on February 1, 2026
