_Follow along with the video lesson:_ --- ### Exploit - Oracle Manipulation - Minimized To glean a better understanding of Oracle Manipulation as a vulnerability and potential exploit, let's take a look at the examples provided in our [**sc-exploits-minimized**](https://github.com/Cyfrin/sc-exploits-minimized) repo. All of the images and diagrams for this lesson will be in the [**src/oracle-manipulation**](https://github.com/Cyfrin/sc-exploits-minimized/tree/main/src/oracle-manipulation) directory. First, let's recall what we've been talking about regarding flash loans. These are equity focuses DeFi systems which allow anyone to leverage more than their own buying power for the duration of a single transaction, for a fee. 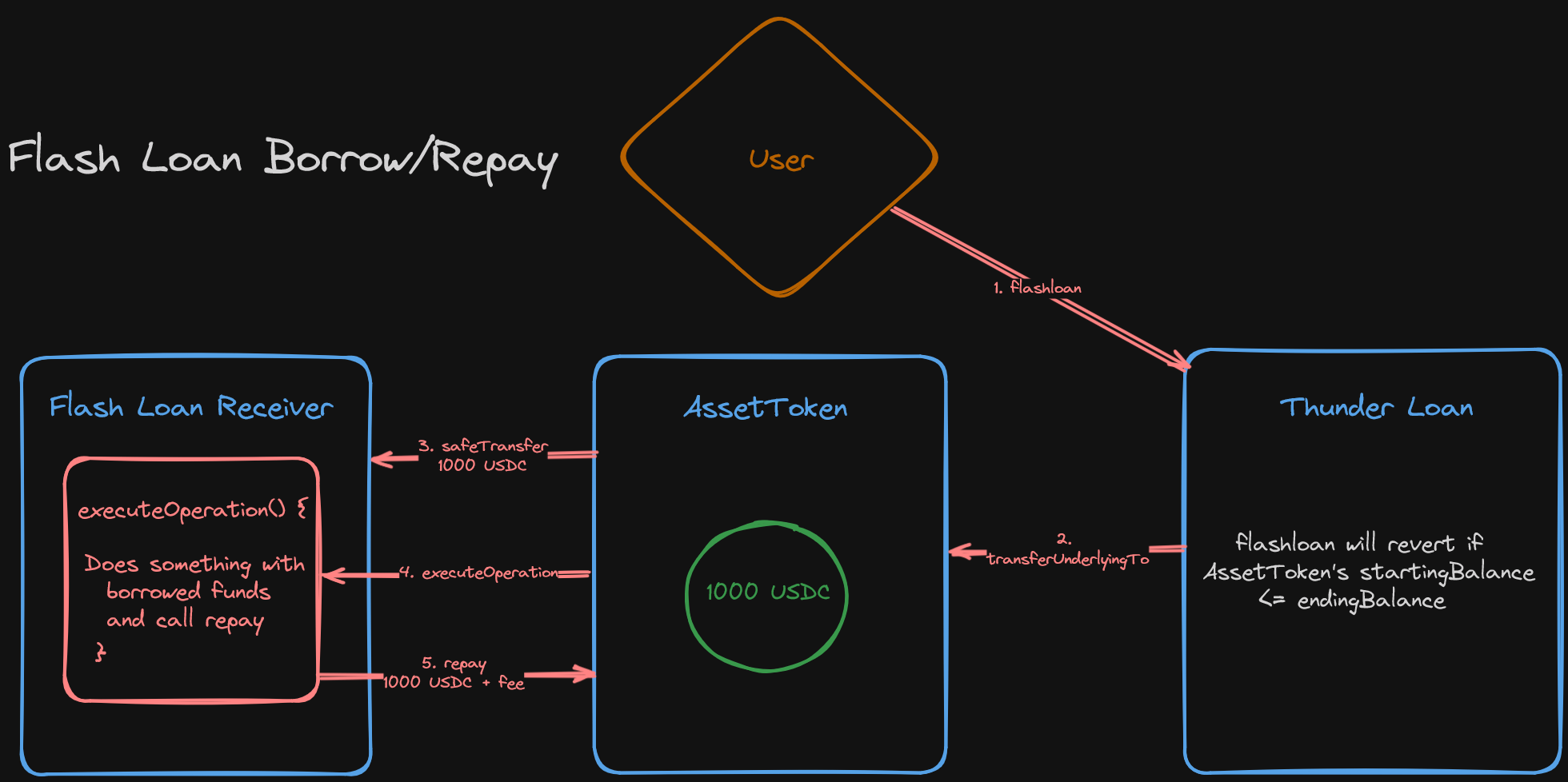 We also learnt that this was an amazing tool to facilitate arbitrage, whereby a user can normalize the prizes between Dexs by buying and selling an asset with an identified price difference between them. This has two effects 1. The user makes a profit denoted by the margin between the two listings of the asset 2. The listed prices of the asset should change as demand and price on each protocol adjusts for the arbitration 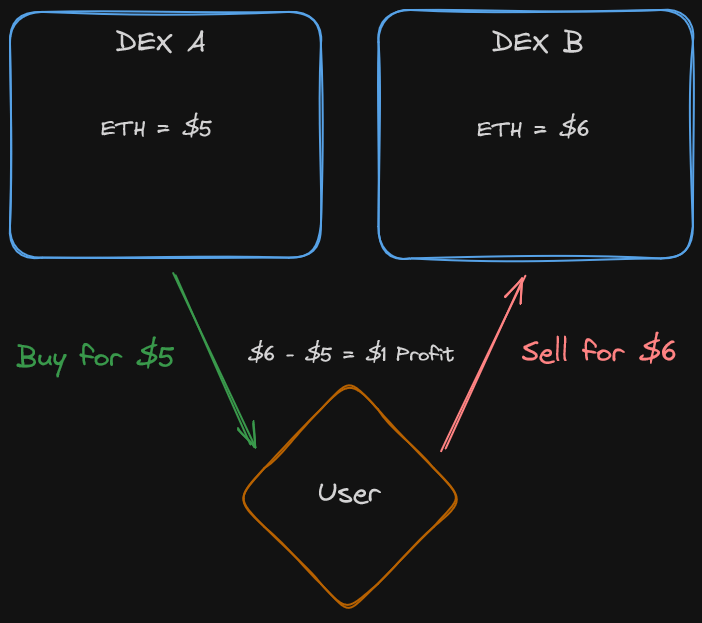 Do you see where we're going with this yet? Flash loans afford the ability to manipulate the prices of assets on Dexs by drastically altering the ratios between trading pairs. This results in any price of an asset reliant on these Dex pairs will be inaccurate! The impact on Thunder Loan itself is a little harder to see, but let's consider that this would look like in a simpler example. We know the flash loan receiver needs to be a smart contract with the executeOperation function. It's in this function that the funds are used for the purpose the user borrowed them, what if they were first used to manipulate a Dex price? 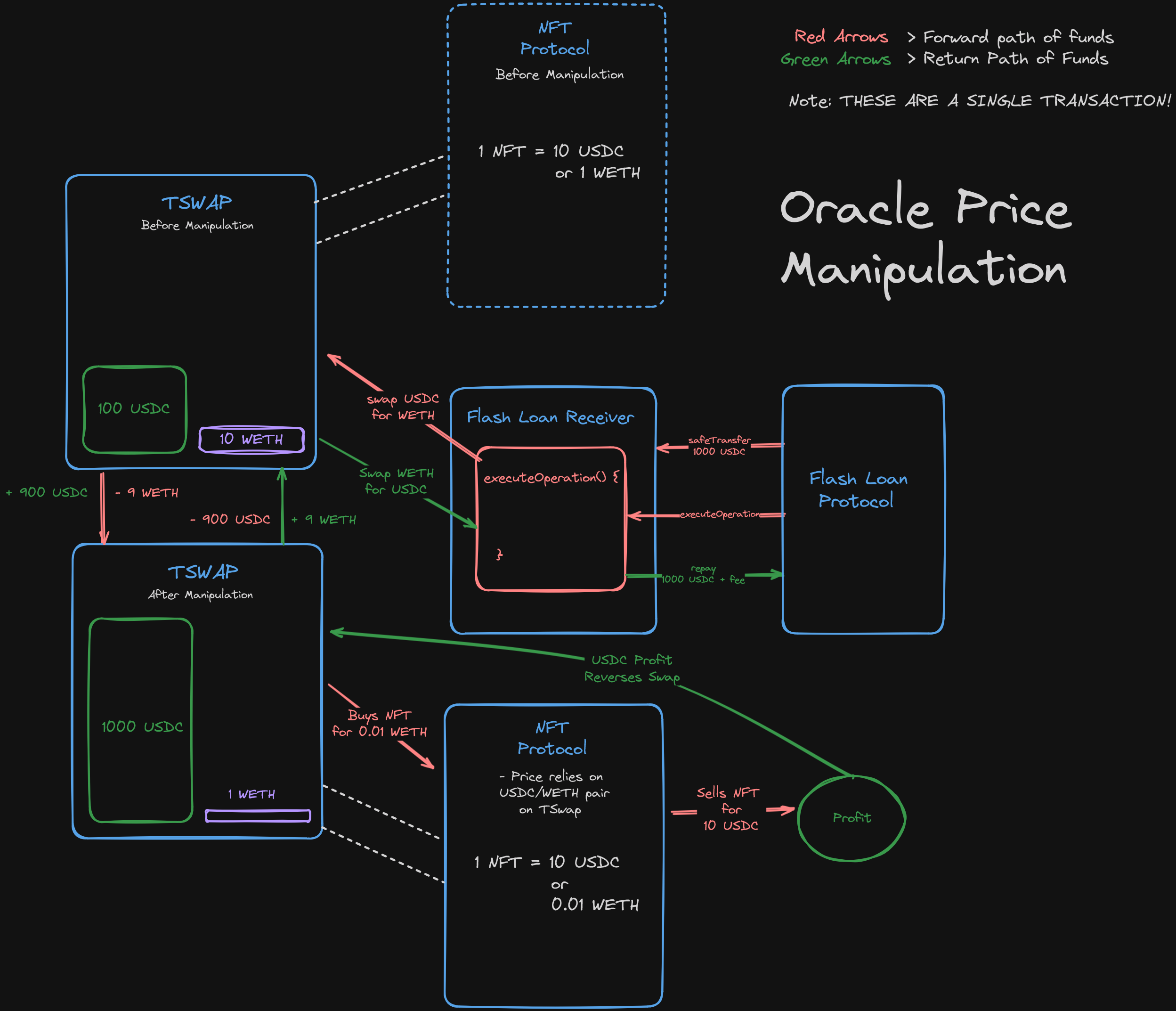 In the diagram above, we can see that an interaction with TSwap is being used to manipulate the price ratio between the two tokens (USDC and WETH). This allows the flash loan receiver to purchase an NFT at a massive WETH discount, ultimately selling it for a profit in USDC. The profit of course is used to then repay the flashloan. It's the NFT Protocol's reliance on a Dex like TSwap as an oracle that leads to a vulnerability like this! > **Note:** The Diagram is simplified, there are other considerations not accounted for such as slippage, the weth spent on the NFT etc, but the concept is the same. ### Wrap Up This is great high-level overview of the vulnerabilities associated with using Dexs like `TSwap` as a `price oracle`. We're going to see this in action within `ThunderLoan` when we write a PoC to highlight this vulnerability. Before jumping into the next lesson, I encourage you to take a look at the contracts and examples provided in [**sc-exploits-minimized**](https://github.com/Cyfrin/sc-exploits-minimized), for this vulnerability. Oracle Manipulation is a big one, so we _have got to_ be familiar with it. The repo has some fantastic examples and links to Remix, [**Damn Vulnerable DeFi**](https://www.damnvulnerabledefi.xyz/) challenges and even a [**great case study**](https://rekt.news/cream-rekt-2/) pertaining to `oracle manipulation`. Please investigate, stay curious! When you're ready, I'll see you in the next lesson where we'll identify how this specifically impacts `Thunder Loan` and we'll construct a write-up (with Poc)! 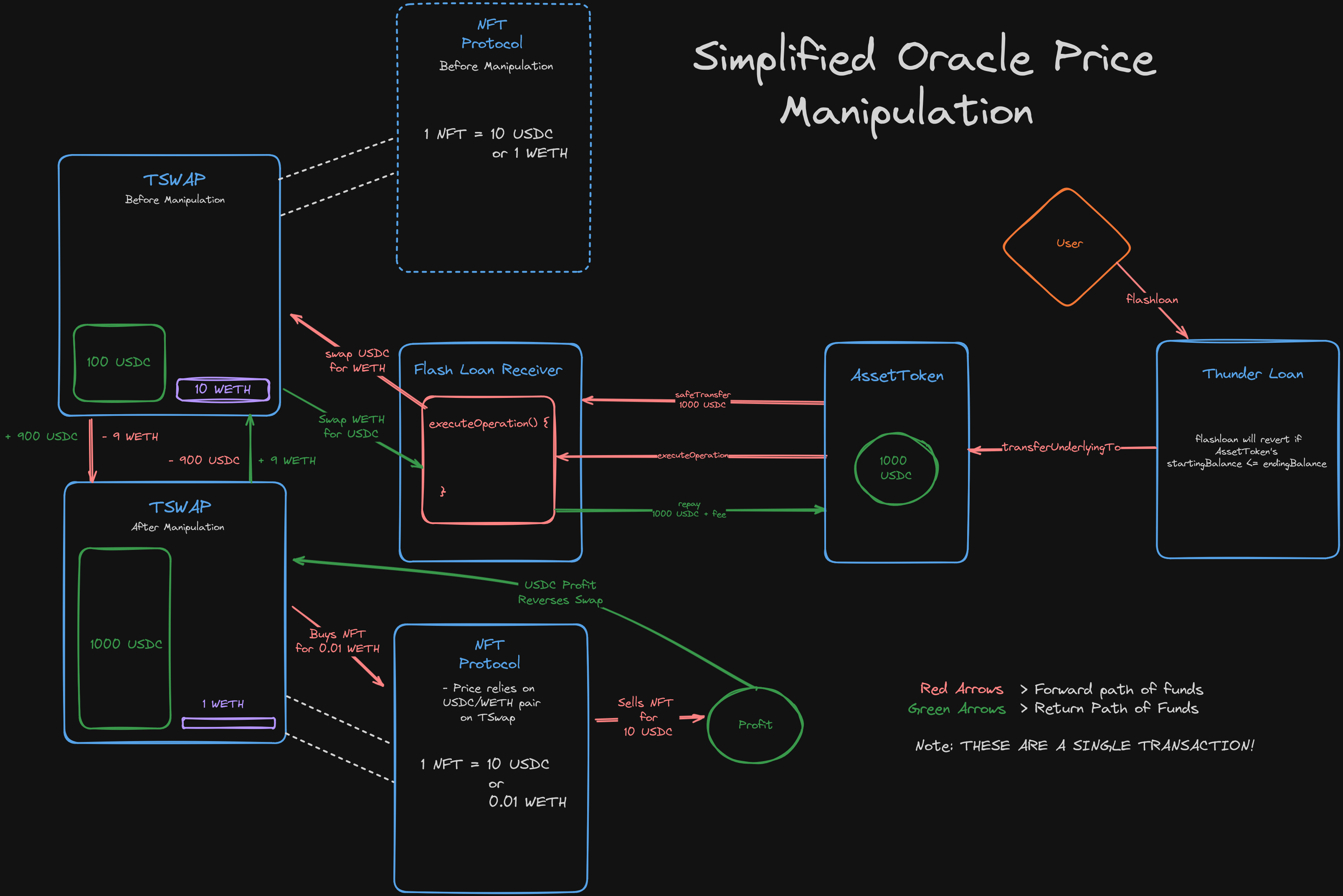
Follow along with the video lesson:
Exploit - Oracle Manipulation - Minimized
To glean a better understanding of Oracle Manipulation as a vulnerability and potential exploit, let's take a look at the examples provided in our sc-exploits-minimized repo.
All of the images and diagrams for this lesson will be in the src/oracle-manipulation directory.
First, let's recall what we've been talking about regarding flash loans. These are equity focuses DeFi systems which allow anyone to leverage more than their own buying power for the duration of a single transaction, for a fee.

We also learnt that this was an amazing tool to facilitate arbitrage, whereby a user can normalize the prizes between Dexs by buying and selling an asset with an identified price difference between them. This has two effects
The user makes a profit denoted by the margin between the two listings of the asset
The listed prices of the asset should change as demand and price on each protocol adjusts for the arbitration

Do you see where we're going with this yet?
Flash loans afford the ability to manipulate the prices of assets on Dexs by drastically altering the ratios between trading pairs. This results in any price of an asset reliant on these Dex pairs will be inaccurate!
The impact on Thunder Loan itself is a little harder to see, but let's consider that this would look like in a simpler example.
We know the flash loan receiver needs to be a smart contract with the executeOperation function. It's in this function that the funds are used for the purpose the user borrowed them, what if they were first used to manipulate a Dex price?

In the diagram above, we can see that an interaction with TSwap is being used to manipulate the price ratio between the two tokens (USDC and WETH). This allows the flash loan receiver to purchase an NFT at a massive WETH discount, ultimately selling it for a profit in USDC.
The profit of course is used to then repay the flashloan.
It's the NFT Protocol's reliance on a Dex like TSwap as an oracle that leads to a vulnerability like this!
Note: The Diagram is simplified, there are other considerations not accounted for such as slippage, the weth spent on the NFT etc, but the concept is the same.
Wrap Up
This is great high-level overview of the vulnerabilities associated with using Dexs like TSwap as a price oracle. We're going to see this in action within ThunderLoan when we write a PoC to highlight this vulnerability.
Before jumping into the next lesson, I encourage you to take a look at the contracts and examples provided in sc-exploits-minimized, for this vulnerability. Oracle Manipulation is a big one, so we have got to be familiar with it.
The repo has some fantastic examples and links to Remix, Damn Vulnerable DeFi challenges and even a great case study pertaining to oracle manipulation. Please investigate, stay curious!
When you're ready, I'll see you in the next lesson where we'll identify how this specifically impacts Thunder Loan and we'll construct a write-up (with Poc)!

Oracle Manipulation: Minimized
Patrick showcases a minimalistic example of the Oracle Manipulation vulnerability.
Previous lesson
Previous
Next lesson
Next
Duration: 25min
Duration: 1h 30min
Duration: 35min
Duration: 2h 28min
Duration: 5h 04min
Duration: 5h 23min
Duration: 4h 33min
Duration: 2h 01min
Duration: 1h 41min