### Exploit - Failure to Initialize - Remix Example Failure to initialize can clear be incredibly impactful. Let's see how the exploit works. The [**sc-exploits-minimized repo**](https://github.com/Cyfrin/sc-exploits-minimized) has a link to a failure to initialize [**example in Remix**](https://remix.ethereum.org/#url=https://github.com/Cyfrin/sc-exploits-minimized/blob/main/src/failure-to-initialize/FailureToInitialize.sol&lang=en&optimize=false&runs=200&evmVersion=null&version=soljson-v0.8.20+commit.a1b79de6.js). <details> <summary>FailureToInitialize.sol</summary> > **Note:** I've added the initializer modifier to our initialize function here. This is omitted in the video version of this lesson. Feel free to copy this contract into your Remix instance. ```solidity // SPDX-License-Identifier: MIT pragma solidity 0.8.20; import "@openzeppelin/contracts/proxy/utils/Initializable.sol"; contract FailureToInitialize is Initializable { uint256 public myValue; bool public initialized; function initialize(uint256 _startingValue) public initializer{ myValue = _startingValue; initialized = true; } // We should have a check here to make sure the contract was initialized! function increment() public { myValue++; } } ``` </details> The example here is very simple, but it should illustrate the potential impact of failing to initialize. Go ahead and compile and deploy `FailureToInitialize.sol` 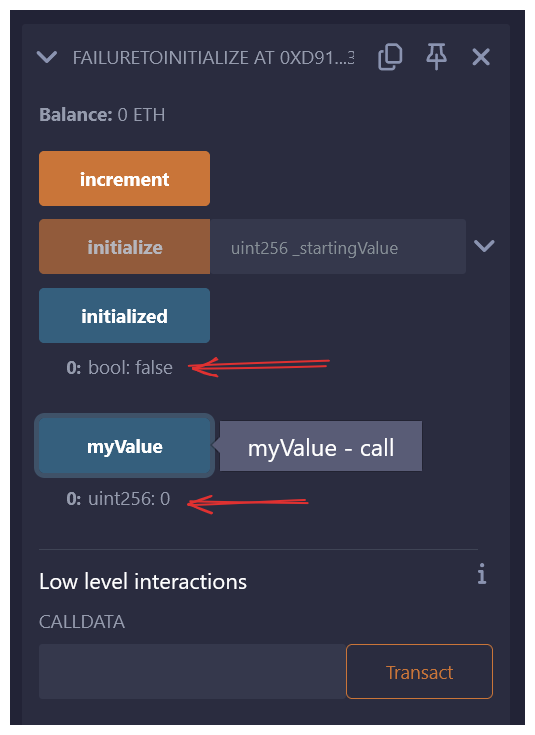 You should see it begin initialized with `myValue` set to zero. If the protocol then proceeds to be used (by calling `increment`), the `initialize` function can be called at any time to overwrite the expected `myValue`. 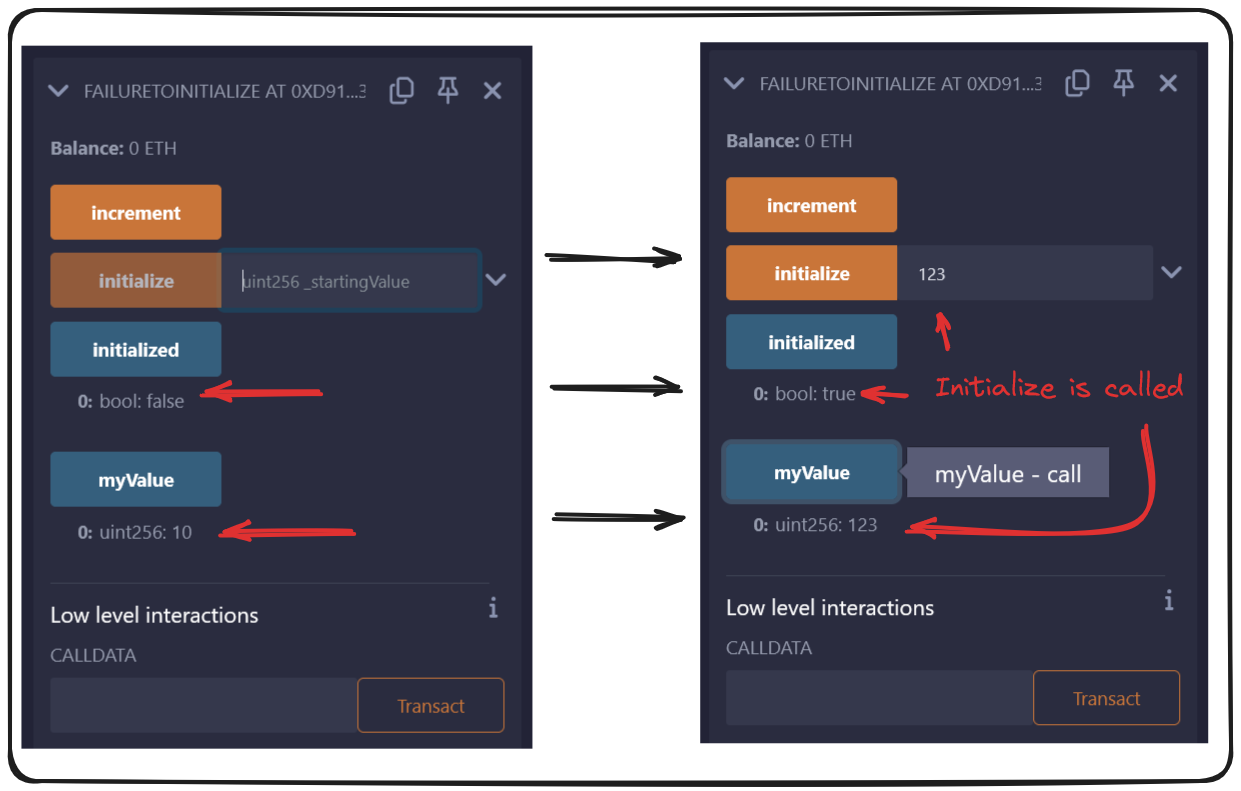 If our `myValue` is changed on us via initialize, we're not even able to re-initialize to fix `myValue` now, effectively breaking our protocol! 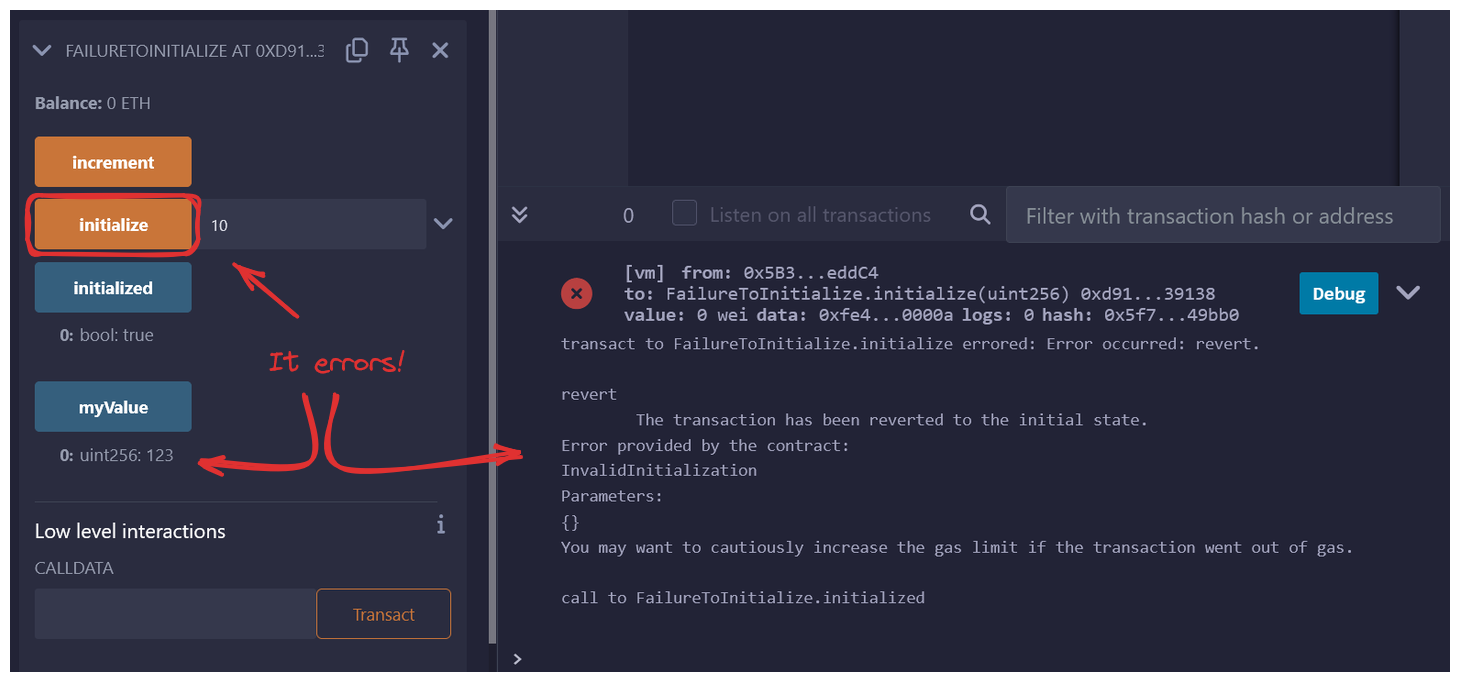 You could imagine a situation like this impacting the management of something very important - like billions of dollars. Failure to initialize can be a very severe attack path depending on the architecture of the protocol and what's being initialized. In the next lesson we'll take a look at a case study where in this exact type of negligence resulted in some pretty severe consequences. Let's go!
Exploit - Failure to Initialize - Remix Example
Failure to initialize can clear be incredibly impactful. Let's see how the exploit works. The sc-exploits-minimized repo has a link to a failure to initialize example in Remix.
FailureToInitialize.sol
Note: I've added the initializer modifier to our initialize function here. This is omitted in the video version of this lesson. Feel free to copy this contract into your Remix instance.
The example here is very simple, but it should illustrate the potential impact of failing to initialize. Go ahead and compile and deploy FailureToInitialize.sol

You should see it begin initialized with myValue set to zero. If the protocol then proceeds to be used (by calling increment), the initialize function can be called at any time to overwrite the expected myValue.

If our myValue is changed on us via initialize, we're not even able to re-initialize to fix myValue now, effectively breaking our protocol!

You could imagine a situation like this impacting the management of something very important - like billions of dollars. Failure to initialize can be a very severe attack path depending on the architecture of the protocol and what's being initialized.
In the next lesson we'll take a look at a case study where in this exact type of negligence resulted in some pretty severe consequences.
Let's go!
Failure To Initialize: Remix
Showcasing the failure to initialize vulnerability within Remix!
Previous lesson
Previous
Next lesson
Next
Duration: 25min
Duration: 1h 30min
Duration: 35min
Duration: 2h 28min
Duration: 5h 04min
Duration: 5h 23min
Duration: 4h 33min
Duration: 2h 01min
Duration: 1h 41min